Serverless Security: Challenges and Solutions
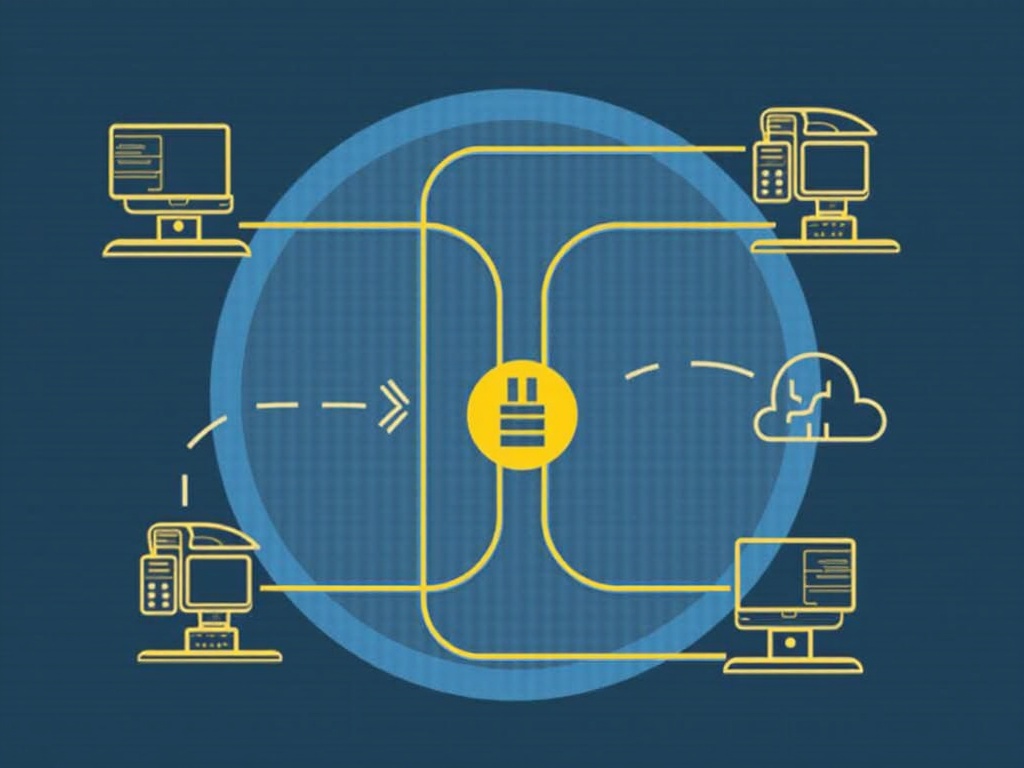
Serverless Security: Challenges and Solutions Serverless computing has revolutionized the way we build applications, allowing us to focus on writing code without worrying about infrastructure management. However, this shift also brings new security challenges that require attention. In this article, we’ll dive into the serverless security landscape, highlighting the challenges and solutions to help you […]