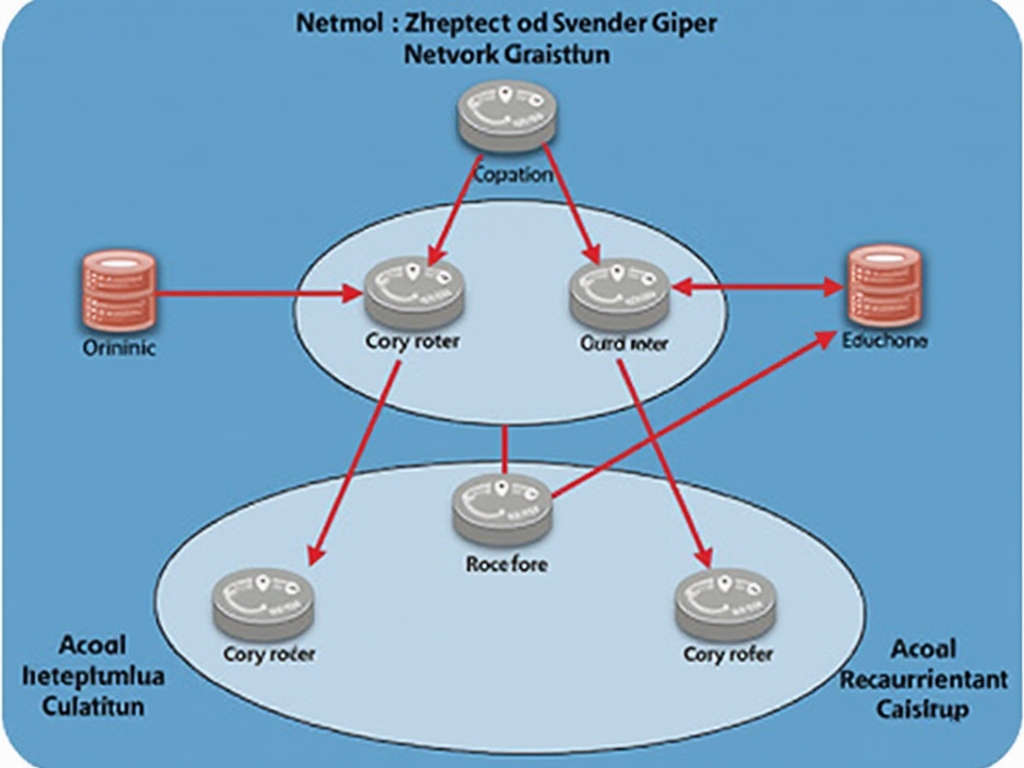
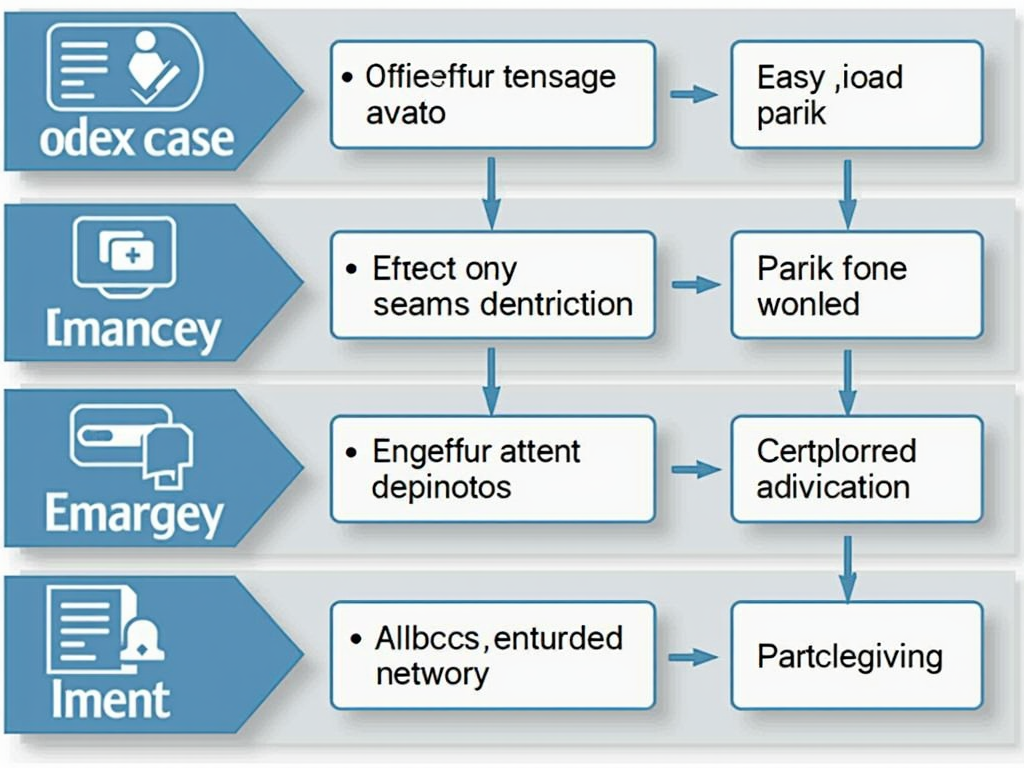
Using Artificial Intelligence (AI) for Predictive Analytics and Secure Development As the world becomes increasingly dependent on technology, the demand for efficient and accurate data […]
Category: Network Security
Tips and tools for securing your network
How to Use Code Review Tools for Security Vulnerability Identification
How to Use Code Review Tools for Security Vulnerability Identification As developers, we are always looking for ways to improve the security of our codebases. […]
Implementing an Effective Secure SDLC Pipeline
Implementing an Effective Secure SDLC Pipeline As software development becomes increasingly complex and interconnected, ensuring the security of the entire lifecycle has become crucial. A […]
Understanding the Importance of Secure Software Development in Businesses
Understanding the Importance of Secure Software Development in Businesses In today’s digital age, software plays a vital role in the success of any business. With […]
How to Use AI-Powered Cybersecurity Solutions for Predictive Analytics
How to Use AI-Powered Cybersecurity Solutions for Predictive Analytics As the digital landscape continues to evolve, cyberattacks have become increasingly sophisticated and frequent. Traditional security […]
Implementing an Effective IoT Security Strategy in Smart Cities
Implementing an Effective IoT Security Strategy in Smart Cities Smart cities are the future of urban planning, where technology and innovation come together to create […]
Understanding the Rise of Cloud-Based Security Threats in Businesses
Understanding the Rise of Cloud-Based Security Threats in Businesses In recent years, cloud computing has become an integral part of many businesses’ operations. With its […]
Using Artificial Intelligence (AI) for Predictive Analytics and Network Security
Using Artificial Intelligence (AI) for Predictive Analytics and Network Security Artificial intelligence (AI) has become increasingly important in various industries, including network security and predictive […]
How to Use Network Isolation and Access Control for Security
Network Isolation and Access Control: A Guide to Securing Your Network In today’s connected world, securing your network is crucial to prevent unauthorized access, data […]
Implementing an Effective Network Segmentation Policy
Implementing an Effective Network Segmentation Policy Network segmentation is a crucial aspect of modern network security. In this article, we’ll explore the concept of network […]