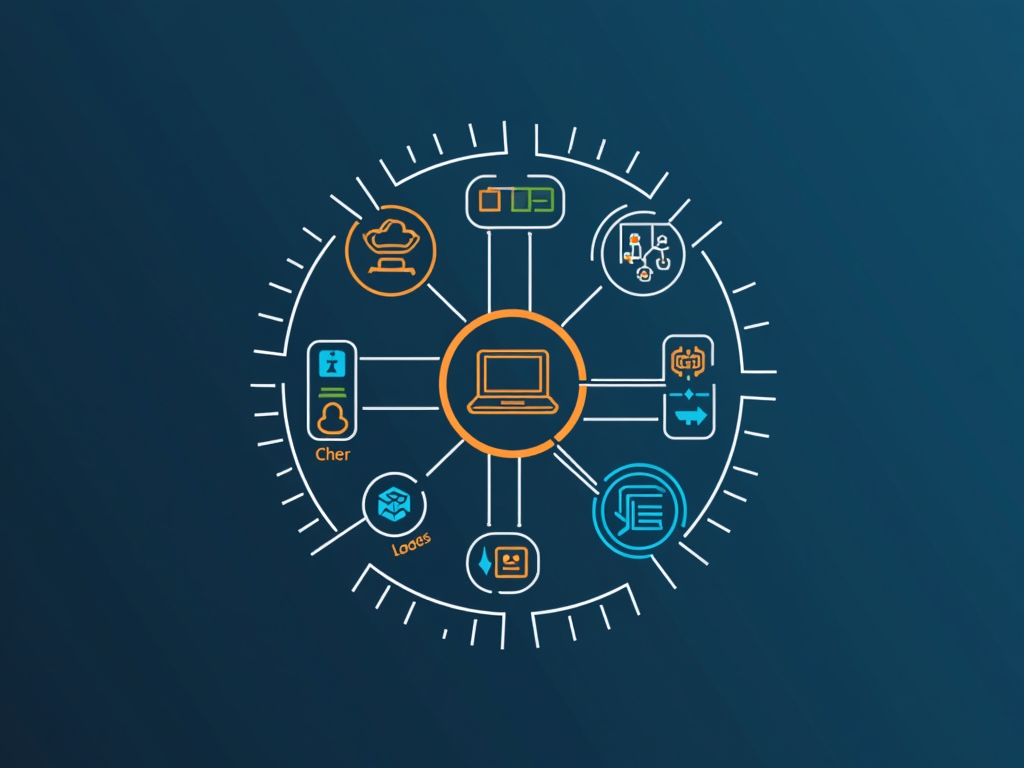
The Benefits of Using EDR Software for Endpoint Security In today’s digital landscape, endpoint security is more crucial than ever. With the rise of remote […]
How to Use a SIEM System for Incident Detection and Response
How to Use a SIEM System for Incident Detection and Response A Security Information and Event Management (SIEM) system is a powerful tool that helps […]
Implementing an Effective IRP (Incident Response Plan)
Implementing an Effective Incident Response Plan (IRP) In today’s digital landscape, cybersecurity incidents are a constant threat to businesses of all sizes. A well-crafted Incident […]
Understanding the Role of Threat Hunters in Corporate Cybersecurity
Understanding the Role of Threat Hunters in Corporate Cybersecurity As cybersecurity threats continue to evolve and become more sophisticated, corporations are recognizing the importance of […]
Using Artificial Intelligence (AI) to Enhance IoT Security
Using Artificial Intelligence (AI) to Enhance IoT Security The Internet of Things (IoT) has transformed the way we live and work, with billions of devices […]
How to Protect Against Cyber Threats Targeting IoT Devices
Protecting Against Cyber Threats Targeting IoT Devices Introduction The Internet of Things (IoT) has revolutionized the way we live and work by connecting devices, sensors, […]
The Benefits of Using a Smart Home Security System
The Benefits of Using a Smart Home Security System In today’s modern world, security is a top priority for many homeowners. With the rise of […]
Implementing Secure IoT Protocols for Connected Devices
Implementing Secure IoT Protocols for Connected Devices With the rapid growth of the Internet of Things (IoT), connected devices are becoming increasingly integral to our […]
Understanding the Risks Associated with IoT Devices in Smart Homes
Understanding the Risks Associated with IoT Devices in Smart Homes In recent years, the concept of smart homes has gained immense popularity, with many homeowners […]
Using Social Engineering Tactics to Test Your Company’s Defenses
Using Social Engineering Tactics to Test Your Company’s Defenses As the world becomes increasingly dependent on technology, cybersecurity threats have become more sophisticated and prevalent. […]