How to Create an Effective Incident Response Plan As technology advances, the frequency and complexity of incidents increase, making it crucial for organizations to have […]
The Benefits of Using Multi-Factor Authentication (MFA)
The Power of Multi-Factor Authentication: Unlocking the Secrets to Enhanced Security In today’s digital landscape, where passwords are no longer sufficient to ensure security, Multi-Factor […]
Implementing a Secure BYOD Policy in the Workplace
Implementing a Secure BYOD Policy in the Workplace As technology continues to evolve, Bring Your Own Device (BYOD) policies have become increasingly common in the […]
Conducting Regular Security Audits for Your Business
Conducting Regular Security Audits for Your Business In today’s digital age, cybersecurity is a top priority for businesses of all sizes. With the rise of […]
Using Segmentation to Improve Network Security
Using Segmentation to Improve Network Security As networks continue to grow and evolve, so do the threats they face. One crucial step in maintaining network […]
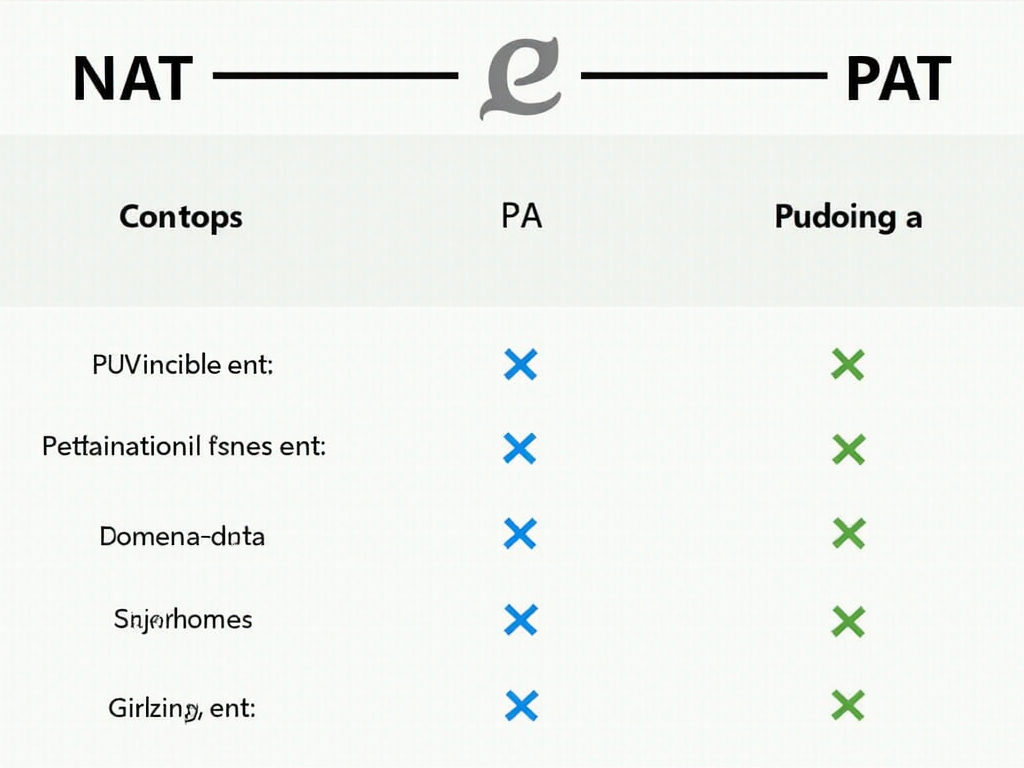
Understanding the Difference Between NAT and PAT
Understanding the Difference Between NAT and PAT As network administrators, we often encounter terms like NAT (Network Address Translation) and PAT (Port Address Translation). While […]
The Impact of IoT Devices on Corporate Networks
The Impact of IoT Devices on Corporate Networks As the Internet of Things (IoT) continues to grow and evolve, it’s essential for organizations to understand […]
Securing Your Network with VLANs and Switches
Securing Your Network with VLANs and Switches In today’s digital age, securing your network is crucial to protect your data and prevent unauthorized access. One […]
Configuring Firewalls for Maximum Protection
Configuring Firewalls for Maximum Protection Firewalls are an essential part of any network security strategy, playing a crucial role in protecting against unauthorized access and […]
The Role of AI in Cybersecurity: Friend or Foe?
The Role of AI in Cybersecurity: Friend or Foe? As technology continues to evolve, the importance of cybersecurity cannot be overstated. With the increasing reliance […]